How to Use Tor Browser on a Mac
Matt Cone September 18, 2021 Tutorials Mac Internet Security
Practically everything you do online with your Mac is logged and traceable back to your computer. Law enforcement officials, internet service providers, and even website administrators can find out what internet services and resources you accessed, when you accessed them, and what computer you used to access them with.

If this lack of privacy sends shivers down your spine, you’ll be happy to hear that there is a way to preserve your anonymity on the internet while using your Mac. The nonprofit Tor project (short for The Onion Router) is a distributed network of volunteers who use their computers to route internet traffic anonymously. Install the free Tor client application on your computer to encrypt information transmitted to or from your Mac, bypass proxies, keep your physical location confidential, and conceal the identity of the sender and recipient.
This guide will help you get Tor up and running on your Mac to protect your privacy and safeguard the information you transmit on the internet. It’s a small step that can provide big peace of mind.
Understanding How Tor Works
Tor uses a technique known as onion routing to conceal a user’s location and pass encrypted messages through a volunteer network of servers around the world. The US Navy created onion routing in 1998 for anonymous communication over a computer network. Today, Tor is used for a variety of purposes by the military, activists, journalists, and people like you.
Onion routing got its name from the data structure, which resembles an onion, as shown in Figure 1. A data packet is first “wrapped” in layers of encryption. As the packet traverses the Tor network, each relay in the network decrypts (unwraps) a layer of encryption surrounding the packet. This prevents the operators of the relays from reading the contents of the packets.
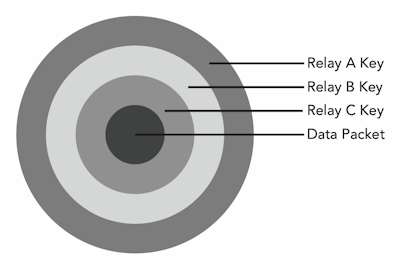
Figure 1. The onion data structure protects messages with multiple layers of encryption to prevent the operators of the relays from reading the contents of the message.
The Tor routing process is illustrated in Figure 2. When you send an email, for example, the client application on your computer selects random relays in the network to create an untraceable path to the recipient. (New paths are created every time you create a message.) Since each relay transporting your message is aware of only two other nodes, your identity is protected. No one observing the traffic on the network can tell where the message came from or where it’s going.
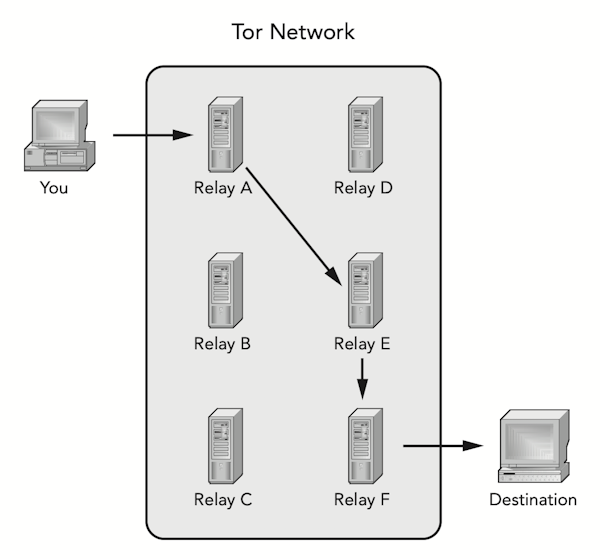
Figure 2. Tor protects against traffic analysis by creating a random path from your computer to the recipient.
As you might imagine, all of this relaying means that Tor can be slow — sometimes painfully slow. Loading a website can take two to four times longer than it would without Tor. For this reason, it’s a good idea to save Tor for those occasions when you absolutely have to remain anonymous and keep your message confidential.
Surfing the Internet Anonymously with Tor
Most people just want to use Tor to browse the web anonymously, without fear of being monitored or tracked. For this reason, the Tor project has created a self-contained package called the Tor Browser for Mac, which includes everything you need to browse the internet safely on your Mac. (There are also browsers for computers running Windows and Linux.)
This is the best option for home users who want to get started with Tor fast. And because the browser can be copied to a USB drive, you can use it at school or work to protect online activities there, too.
Here’s how to use Tor to surf the internet anonymously with your Mac:
Download and install the Tor Browser for Mac on your computer.
Open the Tor Browser application and click the Connect button to connect to the Tor network, as shown below.
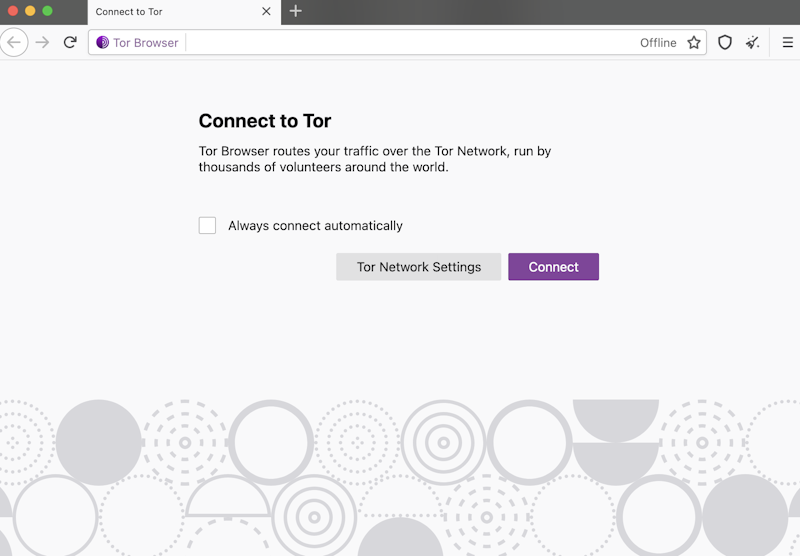
After the Tor Browser connects to the Tor network, you’ll see the screen below.
Now you’re ready to anonymously browse the internet. Those of you who are old enough to remember phone lines and modems might feel like you’re using a 56k modem again. This is one of Tor’s main drawbacks — its network is just not as efficient as the unencumbered switched network that is the internet.
Checking Tor’s Connection
To verify that Tor is working, you can click the lock icon in the address bar. The relays that Tor is using to connect you to the website are displayed in the menu, as shown below.
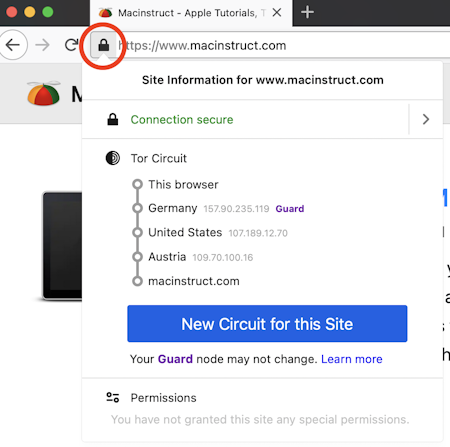
Changing Tor’s Security Settings
The default Tor Browser settings do a good job of protecting your anonymity. But for the truly paranoid, the Tor Browser provides additional security settings that can make your browsing experience even safer. Here’s how to enable to stricter security settings in the Tor Browser:
From the Tor Browser menu, select Preferences.
From the sidebar, select Privacy & Security.
Scroll down to the Security section and select a stricter security setting, as shown below.
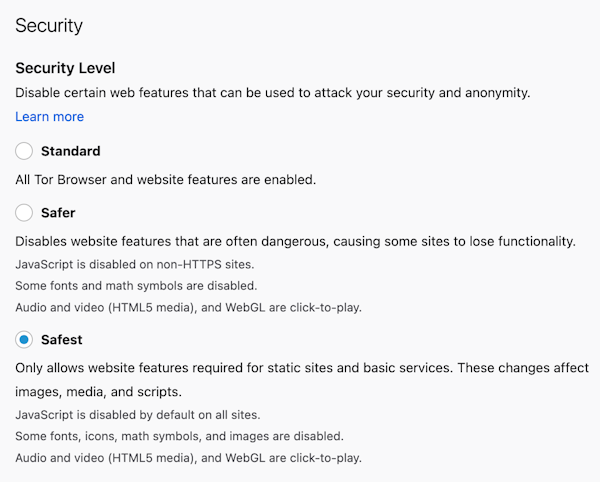
The Tor Browser is now set to use the security setting you selected.
Things to Keep in Mind While Using Tor on Your Mac
Like any application or protocol, Tor is vulnerable to attacks — even some that could compromise your anonymity. For this reason, it’s a good idea to watch out for some common pitfalls:
- Do not use Tor to engage in illegal activity.
- Be careful when using browser plug-ins with the Tor Browser. Some extensions will record and transmit your IP address.
- Tor encrypts your data only to the exit relay — it’s your responsibility to ensure that sensitive data is encrypted the rest of the way. Use HTTPS whenever possible.
Related Articles
Subscribe to our email newsletter
Sign up and get Macinstruct's tutorials delivered to your inbox. No spam, promise!